Authentication feature for CDAP on Kubernetes deployment
Checklist
- User Stories Documented
- User Stories Reviewed
- Design Reviewed
- APIs reviewed
- Release priorities assigned
- Test cases reviewed
- Blog post
Introduction
Currently CDAP has Authentication feature for Standalone and Distributed deployments. Up until now there was no such functionality in CDAP running on Kubernetes. This feature is about bringing this capability in so that all deployments have Authentication feature available for the users.
Goals
Enable Authentication capability for CDAP on Kubernetes deployment.
User Stories
- As an engineer I want to be able to configure CDAP on Kubernetes with enabled Authentication so that I can make my deployment secure.
Design
Description
Changes on CDAP repository
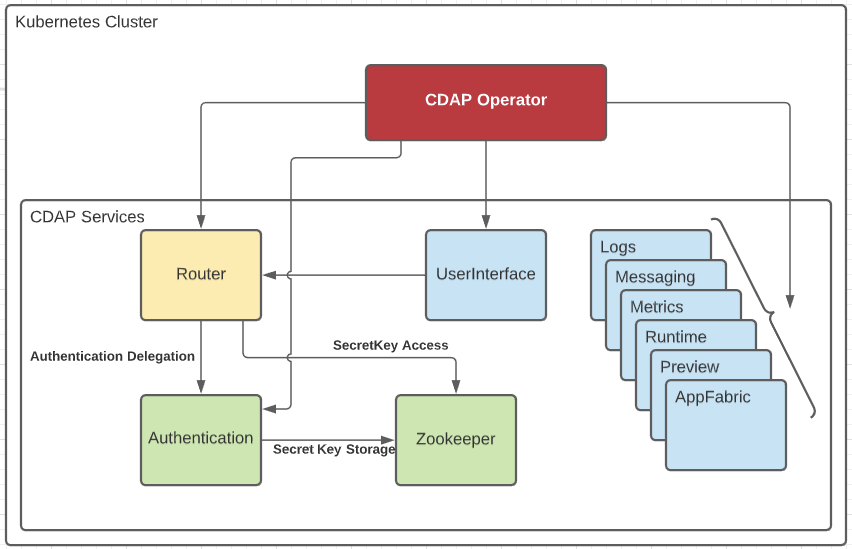
Introduce a new class similar to one of the *ServiceMain classes (any class that extends from the AbstractServiceMain class) for starting the Authentication server. The code is very similar to the AuthenticationServerMain class, except the differences in Guice bindings and added dependency on Zookeeper for secret key propagation. Update RouterServiceMain class to depend on Zookeeper for access to the secret key and use distributed Security module when security is enabled.
Changes on CDAP Operator repository
An update to the CDAP operator https://github.com/cdapio/cdap-operator to introduce a new optional Authentication service, similar to the "Runtime" service.
High Level design
Approach
Approach #1
Approach #2
API changes
New Programmatic APIs
None
Deprecated Programmatic APIs
None
CLI Impact or Changes
None
UI Impact or Changes
None
Security Impact
Application will be more secure since owners of the platform will be able to enable authentication
Impact on Infrastructure Outages
No impact on infrastructure outages.
Test Scenarios
| Test ID | Test Description | Expected Results |
|---|---|---|
Releases
Release X.Y.Z
Release X.Y.Z
Related Work
- Work #1
- Work #2
- Work #3
Future work
Related content
Created in 2020 by Google Inc.