| Note |
|---|
Note: This topic is no longer supported. |
CDAP Ranger Authorization Extension
Apache Ranger is centralized security framework used to manage authorization privileges.
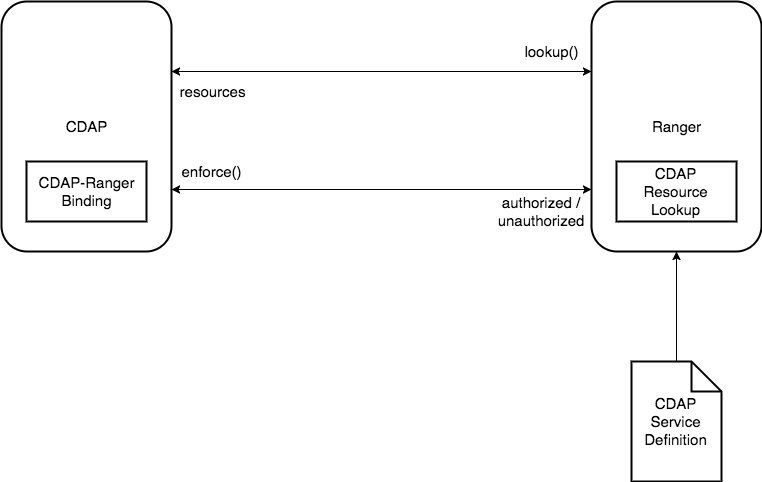
Architecture
CDAP Ranger extension consists of three major components:
CDAP Ranger Loookup: Enables Ranger to lookup CDAP entities.
CDAP Ranger Binding: Enables CDAP to use privileges in Ranger for enforcement.
CDAP Ranger Service Definition: Defines CDAP as a service and it's resources in Ranger.
Installation
Before enabling CDAP Authorization please read the following documentation.
Installing CDAP Lookup in Ranger
Create a new folder called
cdapunder your Ranger plugins directory. Typically on Ambari clusters it is: /usr/hdp/current/ranger-admin/ews/webapp/WEB-INF/classes/ranger-pluginsmkdir cdap
cd cdap
Move the CDAP Ranger Lookup jar to the cdap plugin directory created above.
mv path-to-jar/cdap-ranger-lookup-[version]-jar-with-dependencies.jar ./
Change permission to the cdap plugin directory (if required)
chown -R ranger:ranger cdap/
Restart Ranger service
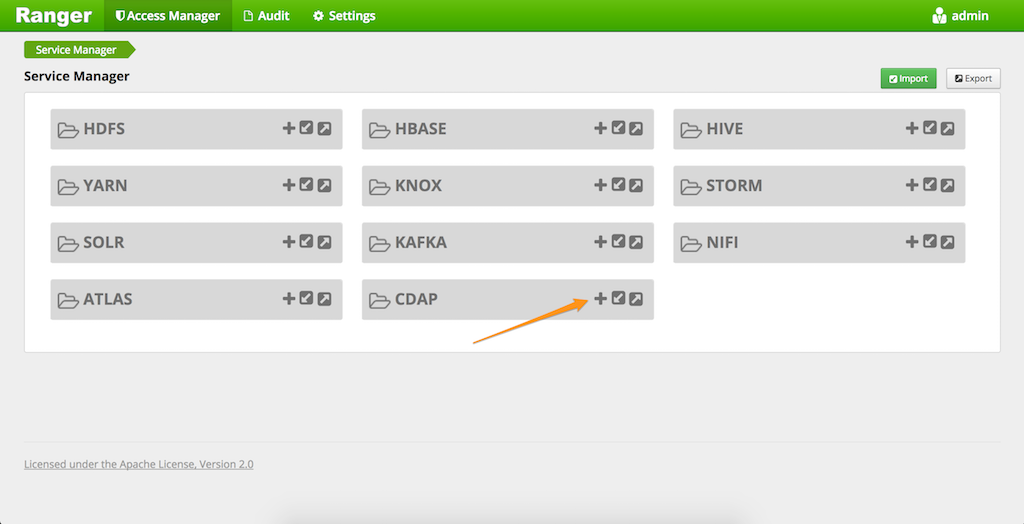
Adding CDAP as a service in Ranger
You can use the `ranger-servicedef-cdap.json <https://github.com/cdapio/cdap-security-extn/blob/develop/cdap-ranger/cdap-ranger-lookup/src/main/resources/ranger-servicedef-cdap.json >`__ to add CDAP as a service in Ranger
curl -u ranger-admin-user:ranger-admin-password -X POST -H "Accept: application/json" -H "Content-Type: application/json" -d @ranger-servicedef-cdap.json http://rangerhost:rangerport/service/plugins/definitions
Now go to the Ranger Admin UI and click on the + button for CDAP service.
Fill in the details of your CDAP instance.
Configuration | Definition | Example |
|---|---|---|
Service Name | Name of this service | cdapdev |
Username | Username to use to connect to cdap instance | username |
Password | Password for the above user | password |
Instance URL | CDAP instance URL | mycdaphost:router-port |
Add New Configuration |
|
|
policy.download.auth.users | User allowed to download policies | cdap |
policy.grantrevoke.auth.users | User allowed to grant/revoke | cdap |
Note: CDAP username and password is only needed if you want lookup of (auto completion of entity names) CDAP entities in Ranger Admin UI. This user must have authorization for the entities to be able to look it up. Please see documentation below on how to add these privileges. Although, it is not necessary for this user to have authorization on all entities. In this case you will not be able to use auto completion of entity names in Ranger Admin UI and will have to type complete entity names.
...
Optional: As mentioned earlier if you want Ranger to be able to lookup CDAP entities you will need to give the connecting user specified during service definition ANY (READ, WRITE, EXECUTE or ADMIN) privilege on all entities. You can just go ahead and add that user with some permission to the above existing policies. Note: This is an optional step. You can still use CDAP Ranger Extension without granting the above connecting user ANY privilege on all the resource although you will not be able to use lookup feature in Ranger and will have to manually type complete entity names.
...
Installing CDAP Authorization Binding for Enforcement
Put the Ranger CDAP configuration xml files under some path which is accessible to
cdapuser. For example:mkdir /usr/local/ranger-cdap-conf
Put the following three files in this directory
...
3. Edit the ranger-cdap-security.xml file
Configuration | Definition | Example |
|---|---|---|
ranger.plugin.cdap.policy. rest.url | Name of this service | http://rangerhost: port |
ranger.plugin.cdap.service .name | Service name given in Ranger while adding CDAP | cdapdev |
4. Give cdap user permission on the above created directory and configuration files
...
7. Save and Restart CDAP.
Policy Management
Policies on mid-level entities
CDAP Policies can be managed in Ranger just like other service policies. Please read the Ranger documentation on Policy management to learn more.
CDAP Ranger Plugin allows to grant policies on mid-level entities in CDAP entity hierarchy by specifying * for lower level and marking them as exclude. For example the below screenshot shows the policy on namespace:default. Notice that the value for application and program are * and they are marked as exclude.
...
Wildcard Policies
CDAP Ranger plugin allows to grant wildcard policies on entities. The supported wildcards are * and ?. * wildcard in Ranger matches 0 or more characters. CDAP does not expect wildcard * to match 0 characters (absence of value) so a * should always be prefixed with ?. For example to grant a user privilege on all programs the wildcard value should be as shown below.
...
A Case Study
Consider a common use case for secure environments, especially data lakes:
...
finance namespace. Also, we could assign privileges to groups rather than individuals - that will make our policies easier to manage over time, especially when new operators enter the team, or existing ones leave: that will simply require adding or removing a user from the group.
Conclusion
We have created a namespace that is impersonated by a headless service account; and we have given privileges to a human user to deploy and operate pipelines in the namespace. To summarize all the privileges we had to assign:
...